
WordPress is the most well-liked Content Management System (CMS), and over 529 million sites are built with WordPress.
There are tons of themes and plugins available to customize your site as you want. But building a site is not an end. One of the most important things about a website is security. There are thousands of sites that are being hacked every day and blacklisted by Google.
So if you are very serious about your site, then you just need to pay attention to your WordPress site security. Follow WordPress security tips from the experts to keep hackers away from your site.
WordPress is a well-growing open-source platform, so hackers principally target WordPress sites. You’re not free from this.
Your website can get hacked if you do not care about your site’s security. Like different things, you furthermore need to check your site security frequently.
- Why WordPress Security is Important?
- How hackers break into WordPress websites
- WordPress Security Tips to Protect Your Website
- 1. Choose a Secure WordPress Hosting Provider
- 2. Keep WordPress Core, Themes, and Plugins Updated
- 3. Don’t Ever Use Nulled Theme or Plugin
- 4. Use Strong Passwords and Two-factor Authentication
- 5. Change the WordPress Admin Login URL
- 6. Limit Login Attempts
- 7. Enable SSL / HTTPS
- 8. Disable File Editing
- 9. Install a Reliable WordPress Security Plugin
- 10. Hide the WP-config.php and .htaccess files
- 11. Take Regular Backups
- 12. Use a Web Application Firewall (WAF)
- 13. Remove Unused User Accounts and Assign Proper Roles
- 14. Run Regular Security Scans
- 15. Hardening Steps Every WordPress Site should Use
- 16. Monitor Activity and Logs
- 17. Post-hack Checklist: Quick Recovery Steps
- 18. SEO and Reputation After a Hack
- Conclusion
- FAQ
Why WordPress Security is Important?
Your site may be too small to attract attackers. That is a common belief. In truth, hackers hunt for easy targets.
They use automated tools that scan thousands of sites every hour. Sites with weak passwords, old plugins, or insufficient file permissions are first on the list. Attackers look to inject spam, steal data, or plant malware to get access to your site.
The fallout from a hack goes beyond downtime. Search engines can block a site. Visitors will not trust it, and they will feel that their data is no longer safe there.
If you run an online store, customers may lose trust after a breach. Even a personal blog will lose search rankings when it gets flagged for malware. Fixing a hacked site can take several days. It may also require professional help.
Security pays for itself. Investing a small amount in the right tools and practices prevents bigger losses. Start with the basics: good hosting, updates, backups, and strong login controls. The rest builds on those steps.
How hackers break into WordPress websites
Understanding common attack paths helps you block them. Here are the usual suspects:
- Outdated plugins and themes. Many vulnerabilities live in third-party code. Attackers exploit those holes. Research shows that a large share of WordPress security issues comes from plugins.
- Weak passwords. Brute-force tools try common passwords on the wp-admin. Weak or reused passwords are lost fast.
- Unpatched WordPress core. While core gets regular fixes, delaying updates leaves you exposed.
- Bad hosting or server setup. Shared hosts with poor isolation make it easier for attackers to move between sites.
- Misconfigured permissions and exposed files. Files like wp-config.php hold secrets. If left unprotected, they leak database credentials.
- Malicious or nulled plugins. Using pirated plugins can bring backdoors and malware. Avoid them.
Attackers often combine methods. For example, they find a vulnerable plugin, use it as a beachhead, then create admin accounts or plant a backdoor. That makes cleanup harder. The best defence is layered: reduce surface area, control access, and monitor for strange activity.
WordPress Security Tips to Protect Your Website
In this guide, I’m sharing the 10 Best WordPress security tips to keep your website secure from hackers and malware.
1. Choose a Secure WordPress Hosting Provider
This is the most important part to strengthen your WordPress security and safeguard your business. Good web hosting plays a major role in keeping your site secure. A top-rated web host will offer multiple security layers and monitor your site 24/7 for malware and attacks.
Most of the newbies make the first mistake when they buy cheap hosting. They like inexpensive hosting rather than decent hosting. Basically, cheap hosting doesn’t provide any good security function, and its performance is poor as well. This way, hackers can target your site and hack it easily.
Before buying web hosting from any company, check their hosting performance and security services. If they provide good security, you can go for it.
Look for these features when you pick a host:
- Isolation between accounts. Each site should be isolated from others on the same server.
- Regular server-side backups. Hosts that keep independent backups help when an attack gets past site-level protections.
- Built-in firewalls and malware scanning. Some managed hosts include these in their plans.
- Automatic updates for server software. This reduces risks from outdated server components.
- Fast support that knows WordPress. Quick, competent support helps during a security incident.
Managed WordPress hosts provide enhanced security features and automatic updates. They cost more, but they save time and reduce risk for busy owners.
If you must use shared hosting, pick a reputable provider with clear security measures.
2. Keep WordPress Core, Themes, and Plugins Updated
If you are not updating your WordPress versions, plugins, and themes, then you are far behind in security. Staying up with the latest version of WordPress is a good practice.
With every WordPress update, there come many WordPress fixes, security improvements, bug fixes, etc. This is also similar to plugins and themes.
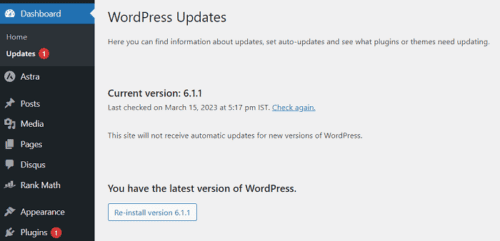
Updating the WordPress version is very easy, and you can do it right from your WordPress admin dashboard. First, go to your WordPress dashboard> Update. From there, you can see what needs to be updated.
Keep these tips in mind:
- Schedule a short, regular maintenance window to check updates.
- Maintain a list of critical plugins and monitor their changelogs.
- Remove plugins and themes that you do not use.
- Avoid nulled or pirated plugins. They often contain malware.
If you manage multiple sites, consider using a management service that supports automated updates and backups. That reduces human error and speeds recovery if an update causes a problem.
3. Don’t Ever Use Nulled Theme or Plugin
This is another key WordPress security tip to protect your website. There is no doubt that premium themes look professional and have more functionalities than a free theme.
Premium WordPress themes are paid and need an activation key to activate them. But there are so many sites that provide free premium themes and plugins, which are dangerous for your site. Many malicious codes are injected and can contain many bad links. So, always avoid such nulled themes.
There are many free themes available in the WordPress theme directory, where thousands of beautiful-looking themes are available.
4. Use Strong Passwords and Two-factor Authentication
A password is the most vital part of website security. Luckily, WordPress can automatically generate complex, alpha-numeric passwords for all users. However, you should make sure that passwords are not shared with others.
If you want to give admin-level access to developers, use plugins like
Temporary Login Without Password and WP Activity Log to protect your websites.
Add two-factor authentication (2FA) on admin accounts. 2FA forces a second step during login, such as a code from an authenticator app or an SMS message. This blocks most brute-force or credential-stuffing attacks.
Practical steps:
- Use a password manager for your team.
- Require 12+ character passwords for admin or editor accounts.
- Enforce password resets for users with suspicious activity.
- Add 2FA for all accounts with publishing or admin rights.
- Turn off the default admin username if it exists.
Plugins like Wordfence, Solid Security, and dedicated two-factor authentication (2FA) plugins make setup simple. When combined with other measures, 2FA stops many attacks at the login screen.
In addition to this, it is recommended to use a VPN tool from the top VPN providers when you’re logging in on public Wi-Fi or an unfamiliar network. This will secure your connection and your sensitive data, like your password, whenever you sign in to your WordPress site.
NordVPN is an excellent VPN that offers many beneficial features. Read this particular NordVPN review and find out why it’s one of the most used VPN by WordPress users.
5. Change the WordPress Admin Login URL
By default, the WordPress login address is “/wp-login.php” or “/wp-admin” and if you have the same, you need to change it.
There are a few reasons to change your default WordPress login address. First of all, if hackers target your site, they will run a brute force attack on your site and try different types of password combinations. The issue is that we’re getting too much spam registration.
If your site is popular, then there is a high chance that you will get hundreds of thousands of SPAM registrations every day. To stop this, you need to change the default login URL. More than that, you can add security questions to your login page for extra security.
When you change the login URL, avoid plugins that break other integrations. Test after changing the path to ensure your payment gateways, XML-RPC usage, or REST API calls still work. If you rely on third-party apps or mobile posting, ensure they can connect after the URL change.
6. Limit Login Attempts
This is another of the best WordPress security tips that you should not miss.
By default, WordPress permits users to log in as many times as they want. So any user can use the login system without any restrictions. Sometimes hackers use a method by running software to decode encrypted data, such as passwords. This is called a Brute force attack.
So, if you add a limit to the login function on your website, users will have a limited number of attempts to log in.
Once they reach their login retry limit, they will be temporarily blocked from using this login function. This will be done by a WordPress login limit plugin.
7. Enable SSL / HTTPS
These days, SSL is advantageous for all sorts of sites. An SSL keeps your site secure, and your site will get an SEO boost in search results.
In case you are running an e-commerce site, an SSL certificate is a must, and a normal SSL costs around $70-$199 per year. Generally, E-business sites collect sensitive data, i.e., passwords, credit cards, etc.
So all the information between the client web browser and web server is delivered in plain text, which can be discernible. So if you use SSL, the SSL encodes the sensitive data, which can’t be decrypted effortlessly. Along these lines, it influences your site to be more secure.
Getting SSL is easier than ever:
- Many hosts offer free Let’s Encrypt SSL. Activate it from your hosting dashboard.
- After installing SSL, force HTTPS on your site using WordPress or your server settings.
- Update internal links and resources to use HTTPS URLs to avoid mixed content warnings.
- Use an SSL checker to confirm your certificate and chain are valid.
8. Disable File Editing
By default, WordPress comes with an inbuilt file editing function from the dashboard, which allows you to edit themes and plugins.
You can access the theme editor by going to Appearance>Editor. Similarly, the plugin editor can be found under Plugins>Editor.
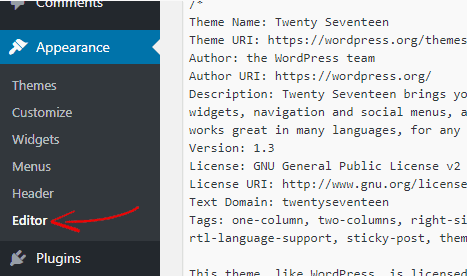
We suggest you disable this feature, as a result of which, if hackers log in to your dashboard, they will inject malicious code into your theme and plugin. So you need to disable the file editing function from your WordPress dashboard.
9. Install a Reliable WordPress Security Plugin
To make your site more secure, you can use a WordPress security plugin. A security plugin monitors your site 24/7, scans for malware, and prevents brute force attacks.
It’s tedious work to check your site security each time, even if you don’t know which file to check, and it is risky as well. So, by using a security plugin, the plugin will take care of all your security.
There are many free WordPress security plugins available that you can use. Key plugin features to look for:
Web application firewall (WAF). Blocks malicious requests before they reach WordPress.
Malware scanning. Scans files and core to detect injected code.
Brute-force protection. Limits failed login attempts and blocks offenders.
File integrity checks. Alerts when core files change unexpectedly.
Security hardening options. Disable file edits, limit API access, and block suspicious IPs.
10. Hide the WP-config.php and .htaccess files
You can hide your WP-config.php and .htaccess files for extra protection of your site.
Many times, hackers target our .htaccess and WordPress config file and destroy our site. To prevent this, you need to hide both files so they cannot be accessed by users.
It is an advanced step, so we recommend that you take a backup of both files.
First, go to your wp-config.php file and add the following code,
<Files wp-config.php>
order allow, deny
deny from all
</Files>
Similar way, add the following code to your .htaccess file,
<Files .htaccess>
order allow, deny
deny from all
</Files>
11. Take Regular Backups
Backups are the last line of defence. If attackers gain access, a clean backup helps you get back online quickly and efficiently.
Set up automated, off-site backups. Keep multiple copies and test your restores.
Backup best practices:
- Off-site storage. Store backups in cloud storage, not only on the same server. Services include Google Drive, Amazon S3, Backblaze, and Dropbox.
- Regular schedule. For busy sites, daily or hourly backups make sense. For smaller blogs, weekly backups may suffice.
- Retention. Keep several versions so you can roll back to a point before the last corrupted snapshot.
- Test restores. A backup is only helpful if it restores cleanly and accurately. Run occasional test restores to a staging area.
Top backup plugins and services include UpdraftPlus, BlogVault, Jetpack (VaultPress), and Duplicator. Each has different pricing and features. If you run an e-commerce site, use a proven solution that supports automatic, frequent backups and easy restores.
12. Use a Web Application Firewall (WAF)
A WAF filters malicious traffic before it reaches your site. It blocks known attack patterns, bot traffic, and some types of exploit attempts. You can choose a cloud WAF or an endpoint (plugin-based) WAF.
- Cloud WAFs run outside your server. They route traffic through a service that filters requests. Cloud WAFs can block attacks even if the server is unpatched. Popular choices include Sucuri and Cloudflare. They often include CDN benefits and DDoS protection.
- Endpoint WAFs are plugin-based and run on your server. They inspect requests at the application level. Wordfence’s firewall is an example. Endpoint WAFs can be effective, but their effectiveness depends on the server’s performance.
A firewall does not replace updates, but it adds an essential layer. For small sites, a cloud WAF from a trusted provider can be a cost-effective way to raise protection quickly. Compare options and pick one that matches your traffic needs and budget.
13. Remove Unused User Accounts and Assign Proper Roles
User accounts are another attack surface. Old or unused accounts with admin access are dangerous. Audit your user list regularly.
Follow these rules:
- Remove inactive accounts, especially those with admin or editor roles.
- Assign the least privilege needed. For example, use Author or Contributor roles for guest writers.
- Review accounts after staff changes and remove access immediately when someone leaves.
- Require strong passwords and 2FA for all privileged users.
Also, consider creating a separate admin account that you only use for site administration. Use a different, non-admin account for daily tasks. This reduces the chance of exposing admin credentials when doing routine posting.
If you run a multi-author site, use an approval workflow and review plugin installations and key settings regularly. That prevents a single compromised user from doing wide damage.
14. Run Regular Security Scans
Security scans find malware, suspicious files, and misconfigurations. Use automated scanners and daily checks to detect issues early. Most security plugins include scheduled scans.
What to scan for:
- Core file integrity and unexpected changes.
- Infected or suspicious files in uploads and theme folders.
- Hidden backdoors and obfuscated code.
- Outdated libraries and known vulnerable plugin versions.
If a scan flags something, treat it as urgent. Some issues are false positives, but you cannot assume that. Quarantine the site (put it in maintenance mode or restrict public access) and make a backup before making changes. Use a second scanner or a professional cleanup service if you are unsure.
If scans reveal repeated infections, investigate the root cause—often a vulnerable plugin or weak credential. Fix the root problem, not just the symptoms.
15. Hardening Steps Every WordPress Site should Use
Hardening adds simple rules that reduce common weaknesses. They are small changes, but effective when combined.
Actionable hardening steps:
- Disable directory listing. Prevent users from browsing folders that expose plugin or theme files.
- Disable XML-RPC if not needed. XML-RPC can be abused for brute-force attacks. Turn it off if you do not use remote publishing or some mobile apps.
- Limit PHP execution in uploads. Prevent execution of PHP files in the uploads folder. Add server rules that block *.php in wp-content/uploads.
- Block access to sensitive files. Use .htaccess or server rules to protect wp-config.php, .env, and .htaccess itself.
- Set secure file permissions. Keep files at 644 and directories at 755. Ensure no directories are globally writable.
These steps take minutes but reduce common exploit paths. Combine them with a security plugin or host-level controls for broader coverage.
16. Monitor Activity and Logs
Tracking site activity helps you spot problems early. Logs show failed login attempts, file changes, and suspicious admin actions.
What to monitor:
- Failed login attempts and IP addresses that try many logins.
- New admin user creation or role changes.
- Unexpected file modifications in core or theme files.
- High CPU or memory usage may indicate malicious scripts.
Use plugins or host dashboards to collect logs. Send critical alerts to email or Slack. Keep logs for several weeks so you can examine events before a breach.
If you detect suspicious activity, block the offending IPs, rotate admin passwords, and run a scan. If you cannot find the cause, restore from a clean backup and consider hiring a professional for cleanup. Logging and monitoring reduce the time between compromise and detection, thereby limiting damage.
17. Post-hack Checklist: Quick Recovery Steps
If a hack happens, act fast and methodically. Panic leads to mistakes. Follow this checklist:
- Take the site offline or enable maintenance mode. This prevents further damage and stops user exposure.
- Create a backup of the current site. Even a hacked snapshot can help forensics. Store it off-site.
- Scan to identify infected files. Use multiple scanners if needed.
- Reset all passwords for admin, FTP, database, and hosting. Rotate API keys and OAuth tokens.
- Restore from a clean backup if available. Ensure the backup is before the breach.
- Update core, plugins, themes, and server software. Patch the vulnerability.
- Harden the site and change keys/salts in wp-config.php.
- Monitor logs and traffic for repeat activity. Keep an eye out for re-infection.
If the hack is serious or you are unable to remove the backdoor, hire a professional cleanup service. A proper cleanup not only removes the malicious files but also identifies the entry point to prevent them from reappearing. Keep a written incident log for future preventative measures.
18. SEO and Reputation After a Hack
A hacked site can lose search visibility quickly. Google and other search engines may display warnings or remove pages from indexing. Cleaning a site is not enough; you must ask search engines to re-crawl and lift warnings.
Steps to recover SEO:
- Request a review. Use Google Search Console to ask for a malware review after cleanup.
- Remove injected spam pages and links. Check sitemaps and robots.txt.
- Regenerate clean sitemaps and resubmit.
- Monitor search traffic and index status. Expect a dip but act to recover quickly.
- Inform users if personal data was involved. Follow privacy rules and regulations for disclosure when required.
Transparency helps. If users may have been affected, notify them with clear steps they should take.
Rebuild trust with transparent updates and demonstrate that you improved security. This reduces long-term reputational damage.
Conclusion
WordPress security is one of the important things you should focus on. If your site gets hacked, you will lose the website forever. So it is better if you secure your site, and in this article, I have written the 10 best WordPress security tips to make your site secure from hackers.
I hope this tutorial helped you fix your security problem. If you’re still having an issue, do let us know.
Do you have any other WordPress security tips to share?
Read Astra Theme Review: Is It The Best WordPress Theme?




